

What Businesses Should Know About HIPAA
By Mark G. Simkin and Jeanne H. Yamamura
In Brief
Anticipating and Preparing for New Requirements
The recently enacted Health Insurance Privacy and Portability Act (HIPAA) affects all businesses to some degree. How it affects the practices of each company, however, may vary considerably. This article outlines why HIPAA is important, describes critical features of HIPAA that businesses should know about, and explains why ignoring HIPAA could be costly. The authors also include a 12-step action plan that a company can follow to ramp up for HIPAA, a list of HIPAA-related deadlines, and websites for additional information.
Although the primary goal of the 1996 Health Insurance Portability and Accountability
Act (HIPAA; Public Law 104-191) was to protect health insurance coverage for
those employees changing or losing their jobs, Congress included certain administrative
changes now becoming effective that will have far-reaching and, most likely,
costly repercussions.
For a business to assume that HIPAA affects only healthcare service providers and insurers is shortsighted: In addition to the healthcare industry, HIPAA also affects those providing certain information or services to or for healthcare providers. For example, a company that performs medical billing or other services involving “protected information” for healthcare providers is governed by the HIPAA privacy requirements.
HIPAA has been described as “the single most significant Federal legislation affecting the healthcare industry since the creation of the Medicare and Medicaid programs in 1965.” Title II of the act introduced mandatory administrative simplification provisions that seek to improve efficiency and effectiveness by standardizing electronic transmissions and to protect the security and privacy of medical information. With these two goals, HIPAA affects not only healthcare providers and insurers, but also every business that has access to medical information as a result of providing goods and services to such entities. Thus, HIPAA affects organizations ranging from medical practitioners, hospitals, and HMOs, to accounting and legal firms, data-processing service centers, and medical suppliers. State, county, and local governments have found it necessary to create task forces to coordinate the efforts required to determine when and where health services are being provided and to identify health information being maintained and transmitted.
HIPAA Requirements
HIPAA applies to all “covered entities,” which the law defines as health plan administrators, health information clearinghouses, and healthcare providers that transmit information electronically. When covered entities contract with others (business associates) to perform some of these functions, contractual arrangements must ensure the privacy of protected health information accessible by business associates.
HIPAA’s requirements address privacy as well as standardization and security. First, HIPAA required the issuance of privacy regulations (known as the Privacy Rule) to protect individually identifiable health information, which became effective April 14, 2003; small providers were given until April 14, 2004. Second, HIPAA required the establishment of national standards for electronic transactions and security, which became effective October 16, 2002, but was extended until October 16, 2003, for small health plans and those filing for an extension. Third, HIPAA issued security standards establishing minimum standards for the protection of electronic health information, on February 20, 2003, with an effective date of April 21, 2005 (2006 for small plans).
A common misconception related to the security standards is that “we don’t have to worry about them until 2005.” Many security controls were actually mandated by the privacy regulations that became effective in April 2003. In particular, the privacy regulations required the implementation of data safeguards.
Under the Privacy Rule, covered entities and business associates are required to ensure adequate protection of all such information. Specifically, HIPAA requires these organizations to do the following:
The practical implications of these mandates are extensive, ranging from the new paperwork required in all healthcare providers’ offices, to IT system revisions, to policy and procedural changes. For example, IT and other personnel will be required to maintain historical files documenting certain requests for information, medical clinic managers may have to consider the types of information requested on sign-in sheets, and hospitals may need to lock storage rooms containing patient files.
In addition to the privacy requirements, HIPAA requires covered entities to do the following:
 Although
this mandate does not include manual records, more than two-thirds of the
nation’s nearly 5 billion medical claims are covered by this law. To
meet HIPAA’s requirements, a business may need to adopt encryption standards
or create private data communications systems for network transmissions. Furthermore,
in most cases, the business will also have to perform periodic audits of systems
to test data integrity and conformity to document transmission standards.
Although
this mandate does not include manual records, more than two-thirds of the
nation’s nearly 5 billion medical claims are covered by this law. To
meet HIPAA’s requirements, a business may need to adopt encryption standards
or create private data communications systems for network transmissions. Furthermore,
in most cases, the business will also have to perform periodic audits of systems
to test data integrity and conformity to document transmission standards.
The electronic transmission and privacy requirements also apply to the business associates of covered entities (i.e., those directly subject to HIPAA requirements). Business associates are entities that perform functions for or on behalf of covered entities which result in access to protected health information. Such services could include claims processing, data analysis, and legal, accounting, consulting, and managerial services. In order to do business with a HIPAA-covered entity, a business associate must itself meet the HIPAA requirements and sign a contract agreeing to establish the necessary safeguards and procedures.
HIPAA’s transmission and privacy requirements are likely to entail changes in the operations of many organizations, and will probably involve considerable investment in training, systems modifications, and new software. Support areas such as administration, communications, and internal audit will also be affected. In the short run, becoming HIPAA-compliant may require large investments of time and money.
Deadlines and Penalties
Exhibit 1 lists some of the HIPAA compliance deadlines. The electronic transmission compliance deadline for health-maintenance organizations (HMO) and other large healthcare providers was October 16, 2002. Although entities were allowed to file for a one-year extension of the deadline, the many that failed to do so are now likely in violation of the transmission requirements. The privacy rules went into effect April 14, 2003. Smaller health plans have an extra year to meet both requirements.
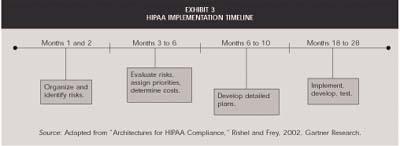
Although the compliance date for the security standards is 2005, many standards were mandated in the privacy rules already in effect. Given that most experts suggest that an organization will need 12 to 18 months to modify its operations, devise solutions, and implement changes, businesses that have not yet started this process are far behind.
To prove it was serious about adopting data transmission standards and safeguarding medical information, Congress included harsh penalties for HIPAA noncompliance. The fines for simple compliance breaches are a maximum of $100 per person per violation, up to $25,000 per person per year. “Knowing misuse” increases these penalties to $50,000 per person and imprisonment for up to one year. Misuse under “false pretenses” or “with intent to financially benefit” increases these amounts to a maximum of $250,000 per person and 10 years imprisonment.
A Far-Reaching Scope
HIPAA’s impact goes far beyond healthcare coverage for displaced workers. The administrative requirements included in Title II of the act potentially affect not only healthcare providers and insurers but the thousands of businesses that also serve the healthcare industry. The major goals of Title II are to protect an individual’s healthcare information and also to standardize the electronic format in which the medical profession transmits such information.
Although large HIPAA implementation costs are expected, large benefits are also anticipated. Experts expect the transaction standardization to reduce data-processing time, speed settlements, and save the industry as much as $9 billion. But it is also likely that becoming HIPAA-compliant will be a time-consuming and costly undertaking. Implementation tasks are wide-ranging and may include the development of new policies and procedures, training staff in privacy and security measures, and upgrading software in order to become HL7 compliant.
A final cautionary note: State laws may preempt HIPAA if the state laws mandate higher levels of information protection, guarantee greater privacy rights, or require more stringent health-information reporting. Those seeking to implement HIPAA must therefore also identify and understand state regulations as well as determine what security, privacy, and EDI transmission standards will satisfy both state and federal law.
©2006 The CPA Journal. Legal Notices
Visit the new cpajournal.com.